Supported Platforms
Incident Management
PagerDuty
Authentication: HMAC-SHA256 (
X-PagerDuty-Signature)On-call management and incident response with native event mapping for incident.triggered, incident.acknowledged, and incident.resolved events.Opsgenie
Authentication: API Key (
Authorization: GenieKey)Atlassian’s alert management with priority mapping and team assignment data.ServiceNow
Authentication: Basic Auth (
Authorization: Basic)Enterprise IT service management with CMDB CI mapping for infrastructure context.Monitoring & Observability
Datadog
Authentication: Bearer TokenFull-stack monitoring with metrics, alerts, and tag-based service correlation.
Grafana
Authentication: Bearer TokenAlert notifications with dashboard links, panel context, and common labels extraction.
Prometheus / Alertmanager
Authentication: Bearer TokenNative Alertmanager webhook receiver with label extraction, grouping support, and Kubernetes metadata.
Splunk
Authentication: Bearer TokenSaved search alerts with result context and search links.
Cloud Provider Alerting
AWS CloudWatch
Authentication: None (SNS)SNS-based alerting with alarm state, metric data, and namespace context.
Azure Monitor
Authentication: NoneCommon Alert Schema support with resource context and severity mapping.
GCP Monitoring
Authentication: Bearer TokenIncident notifications with policy details and resource display names.
APM & Error Tracking
New Relic
Authentication: API Key (
Api-Key)Full-stack observability with issue priorities and entity context.Dynatrace
Authentication: API Token (
Api-Token)Software intelligence with problem impact analysis and AI-detected root causes.Sentry
Authentication: HMAC (
Sentry-Hook-Signature)Application error tracking with issue details, stack traces, and project context.Custom Integration
Generic Webhook
Authentication: Bearer Token (configurable)Fully customizable webhook for any platform. Define your own field mappings using JSONPath expressions.
Platform Roadmap: Don’t see your platform listed? We’re actively adding new integrations based on customer demand. Use the Generic Webhook for immediate integration, or contact support to request a native connector for your monitoring tool.
Setting Up a Webhook Integration
To connect your monitoring and alerting platforms to CloudThinker, follow this step-by-step setup process. The setup wizard guides you through platform selection, webhook configuration, and automatic root cause analysis settings.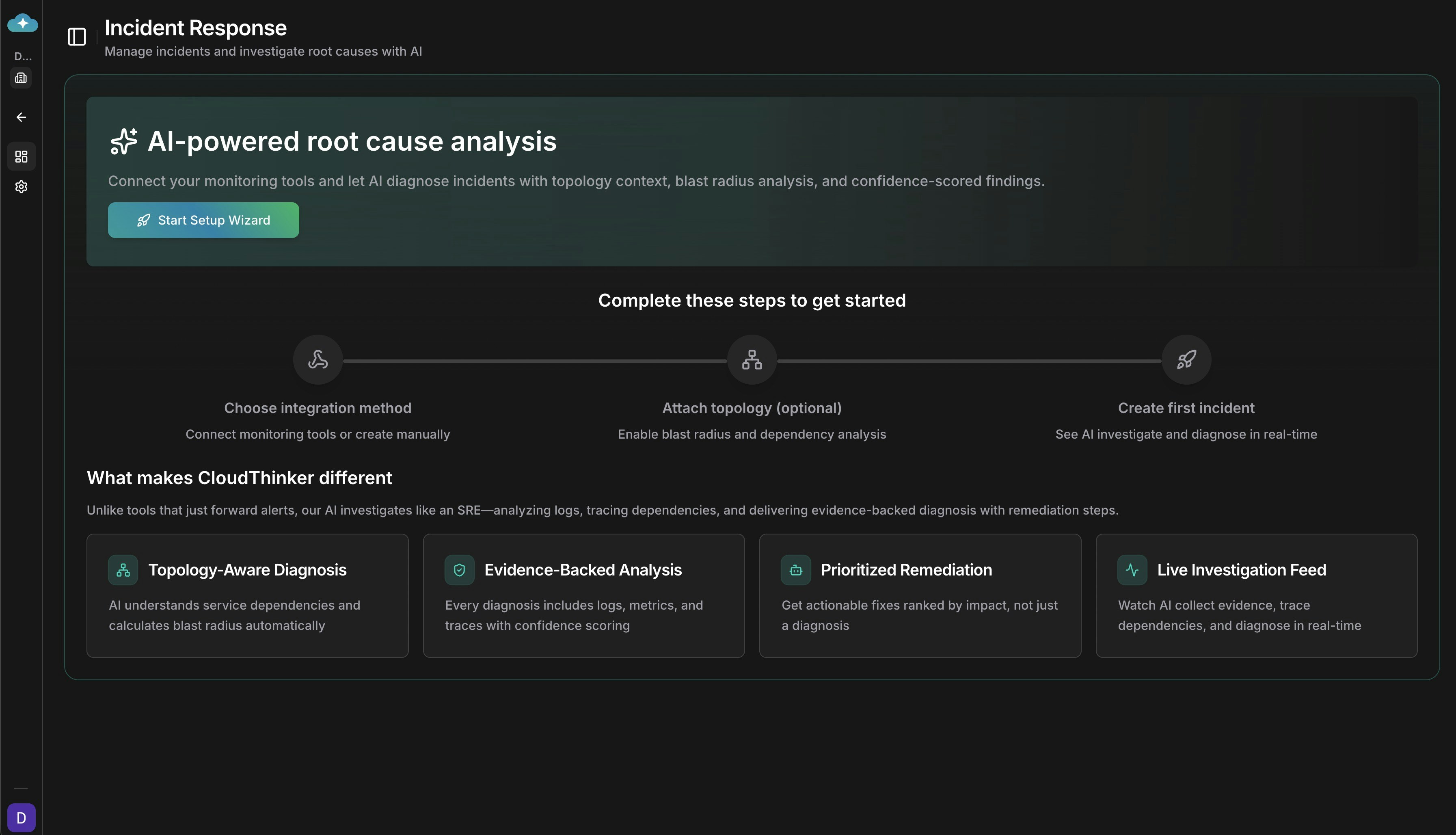
Incident Response dashboard with setup wizard entry point
1
Navigate to Integrations
Go to Incidents → Settings → Integrations tab to access webhook management.
2
Create Webhook
Click Connect on your platform card. The creation wizard opens with platform-specific defaults pre-configured.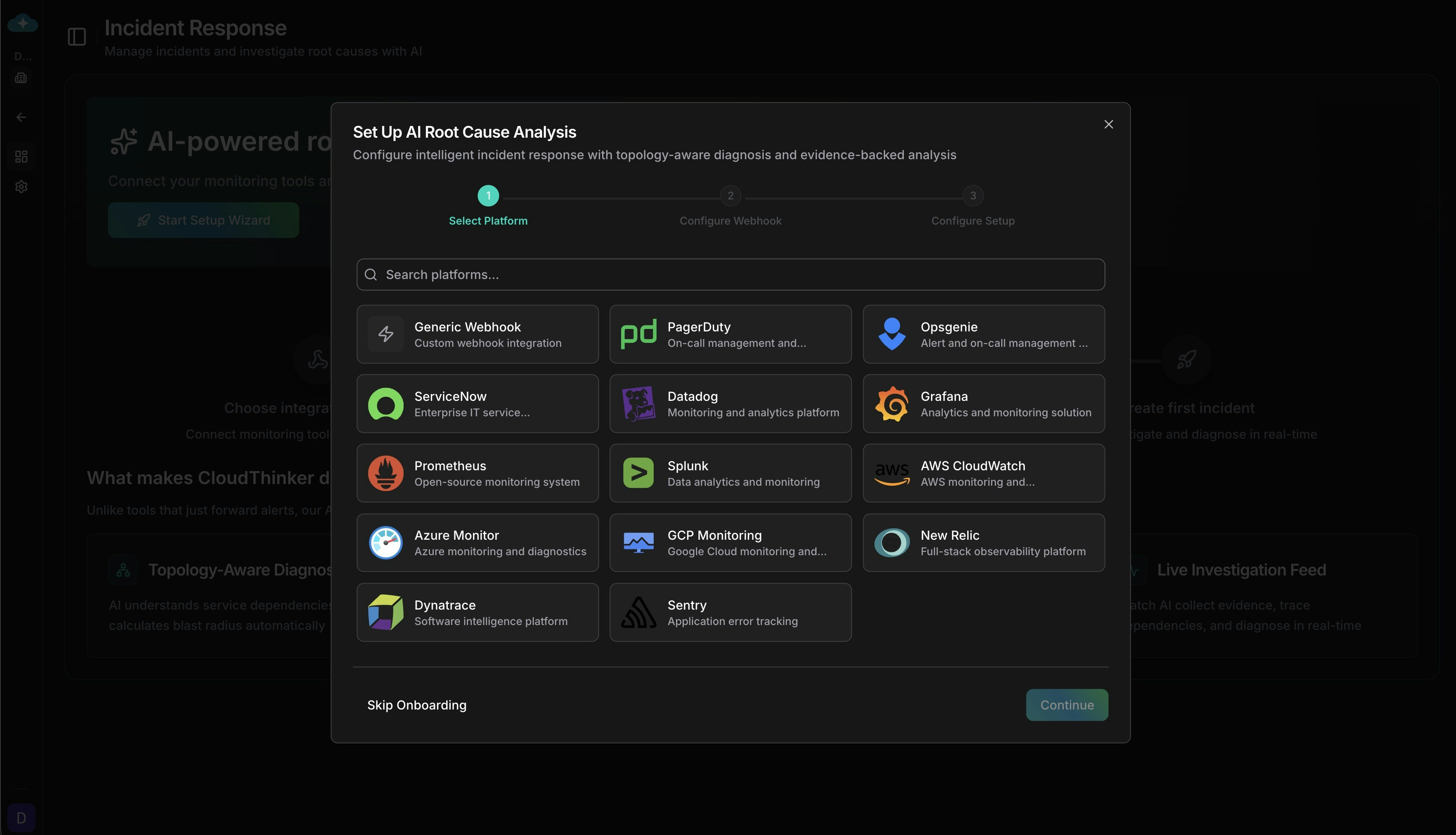

Select your monitoring platform from the available options
3
Configure Basic Info
Enter a name and optional description for your webhook. This helps you identify the integration later.
4
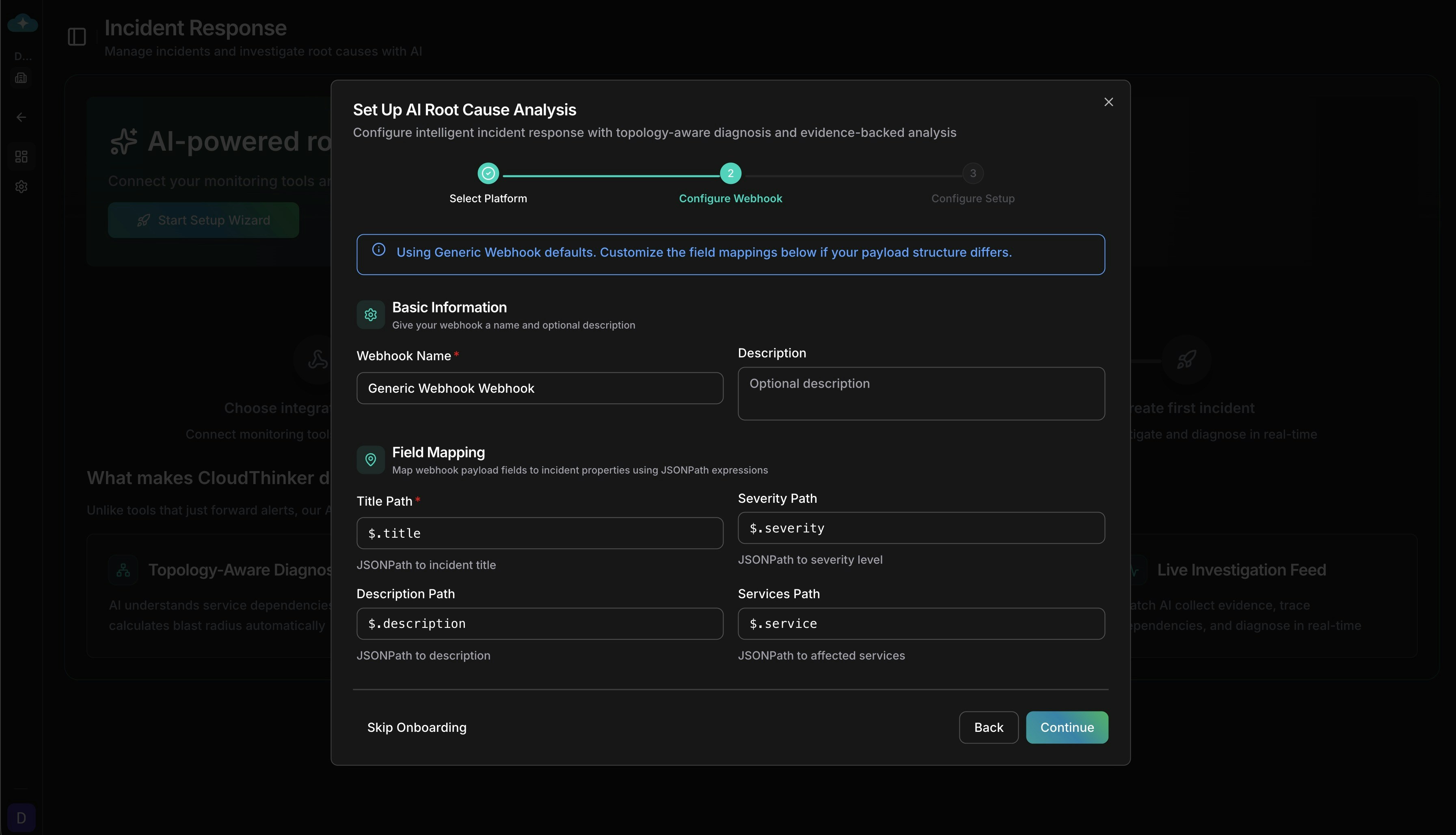
Review Field Mapping
Each platform has pre-configured JSONPath mappings. Customize if needed:
| Incident Field | Example JSONPath | Description |
|---|---|---|
| Title | $.event.data.title | Incident headline |
| Description | $.event.data.description | Detailed information |
| Severity | $.event.data.priority | Critical, High, Medium, Low, Info |
| Services | $.event.data.service.name | Affected service names |

Configure JSONPath field mappings for your webhook payload
5
Configure Auto-Trigger Settings
Customize how incidents trigger root cause analysis: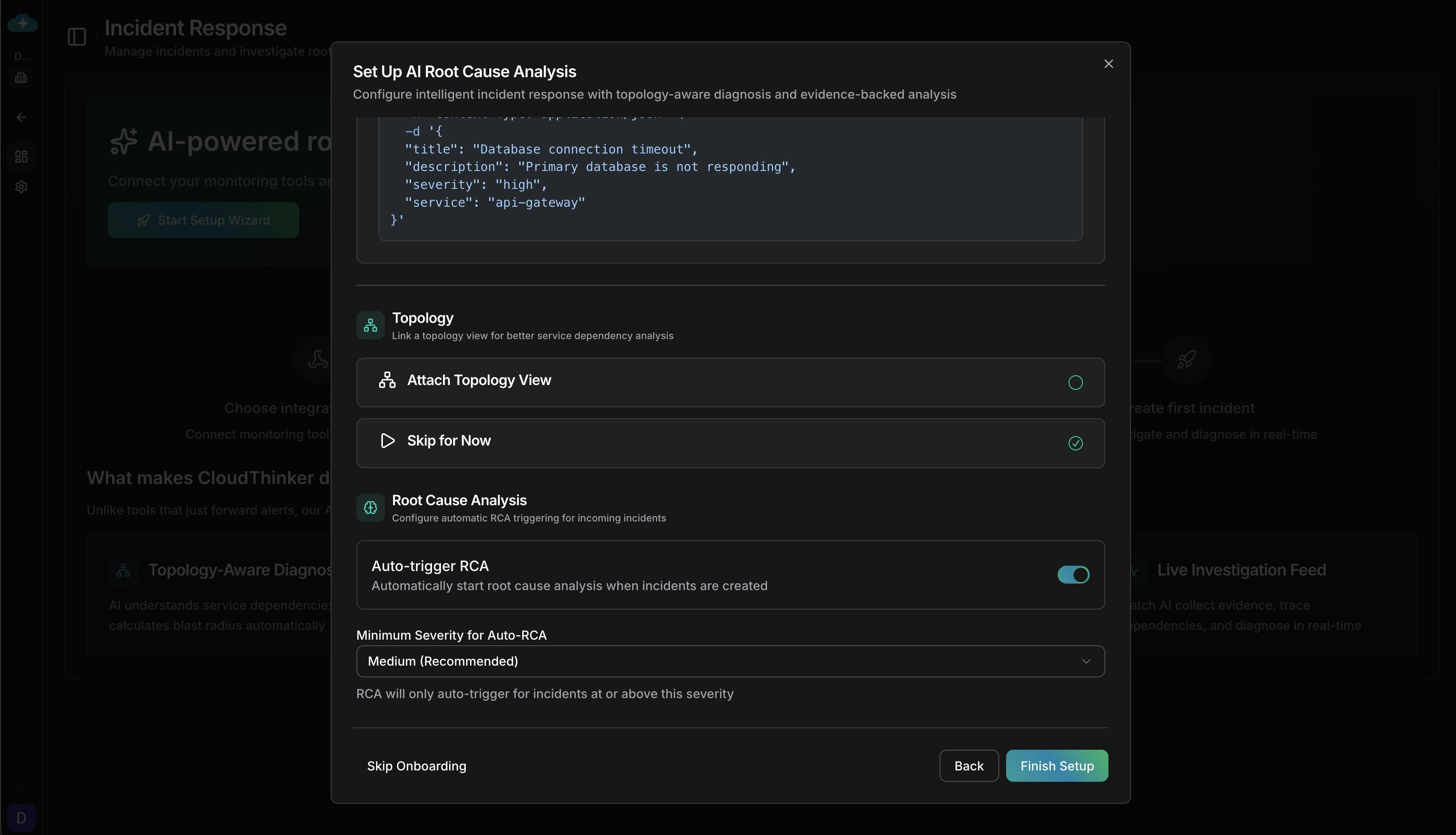
- Auto-trigger RCA: Automatically start AI investigation when incident is created
- Minimum severity: Only trigger RCA for incidents at this severity or higher
- Notify workspace: Send notifications to workspace members
- Enable correlation: Group related alerts into single incidents

Configure automatic RCA triggering and severity thresholds
6
Copy Webhook URL & Authentication
The Setup tab displays your webhook URL and authentication details. Copy these credentials and configure them in your alerting platform.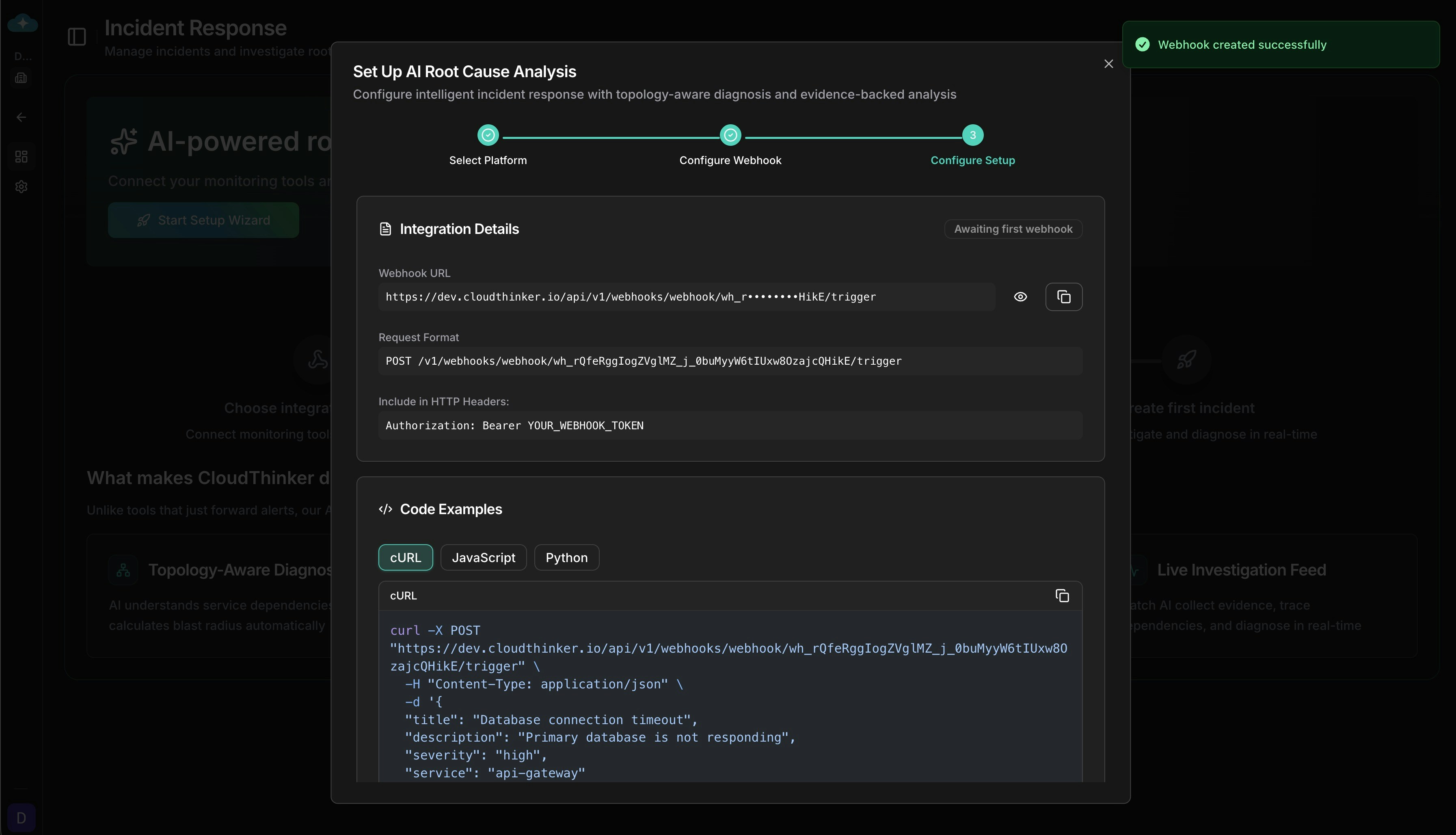

Copy your webhook URL and authentication headers to configure in your alerting platform
Sending Webhooks
cURL Example
JavaScript Example
Python Example
Authentication Methods
CloudThinker supports four authentication methods to match your platform’s requirements:Bearer Token
Standard OAuth-style authentication. Used by Datadog, Grafana, Prometheus, Splunk, and GCP Monitoring.HMAC-SHA256 Signature
Cryptographic payload verification. Used by PagerDuty and Sentry.HMAC-SHA256(request_body, secret_key).
API Key Header
Custom header with optional prefix. Used by Opsgenie, New Relic, and Dynatrace.No Authentication
For platforms that verify subscriptions differently (AWS SNS, Azure Monitor).Platform-Specific Payloads
PagerDuty
- Title:
$.event.data.title - Description:
$.event.data.html_url - Severity:
$.event.data.priority.summary - Services:
$.event.data.service.name
Datadog
- Title:
$.title - Description:
$.body - Severity:
$.alert_type - Services:
$.tags
Prometheus / Alertmanager
- Title:
$.alerts[0].labels.alertname - Description:
$.alerts[0].annotations.description - Severity:
$.alerts[0].labels.severity - Services:
$.alerts[0].labels.service
AWS CloudWatch (via SNS)
- Title:
$.AlarmName - Description:
$.AlarmDescription - Severity:
$.NewStateValue - Services:
$.Trigger.Namespace
Alert Correlation
When multiple alerts arrive within a short time window, CloudThinker automatically correlates them into a single incident.Time Window Correlation
Groups alerts received within a configurable window (default: 5 minutes). Related alerts increment thecorrelated_alert_count metric.
Rule-Based Correlation
Define custom rules to match alerts based on:| Operator | Description | Example |
|---|---|---|
equals | Exact match | service equals "api" |
contains | Substring match | title contains "timeout" |
regex | Regular expression | title regex "^DB.*Error$" |
starts_with | Prefix match | service starts_with "prod-" |
in | Array membership | severity in ["critical", "high"] |
intersects | Array overlap | tags intersects ["production"] |
exists | Field presence | metadata.deployment_id exists |
Correlation Configuration
Deduplication
CloudThinker prevents duplicate incidents using hash-based deduplication.| Setting | Default | Description |
|---|---|---|
| Dedup Key | Auto-generated | SHA256(title + severity + connection_id) |
| Window | 24 hours | Configurable 1-168 hours |
| Behavior | Increment count | Duplicates update webhook_occurrence_count |
Custom Dedup Key
Extract a custom deduplication key from your payload:Security & Limits
Payload Limits
| Limit | Value |
|---|---|
| Max payload size | 100 KB |
| Max field length | 10,000 characters |
| Max array items | 100 elements |
| Max nesting depth | 10 levels |
Rate Limiting
Each webhook has configurable rate limits:- Default: 100 requests per hour
- Configurable: 0 (unlimited) to 10,000 requests per hour
- Response: HTTP 429 when exceeded
Security Features
- Timing-safe signature verification prevents timing attacks
- HTML escaping prevents injection attacks
- Payload sanitization truncates oversized fields
- Sensitive header filtering removes auth/cookie headers from logs
Testing Your Integration
1
Open Test Tab
In the webhook configuration dialog, navigate to the Test tab.
2
Review Sample Payload
Each platform has a pre-configured sample payload. Copy and modify as needed.
3
Send Test
Click Send Test to verify field extraction and authentication.
4
Check Results
Success shows extracted fields. Failure shows specific error details.
Webhook Configuration Dialog
After creating a webhook, configure it through four tabs:| Tab | Purpose |
|---|---|
| Setup | Webhook URL, authentication details, platform-specific setup guide |
| Test | Send test payloads and verify field extraction |
| Field Mapping | Configure JSONPath expressions for incident fields |
| Delivery Logs | Monitor webhook delivery history and response codes |
Troubleshooting
| Issue | Solution |
|---|---|
| Authentication failed | Verify your signing secret or API key matches the source platform exactly |
| Fields not extracted | Check JSONPath syntax—use $.field[0] for arrays, $.field.subfield for nested objects |
| Duplicate incidents | Adjust deduplication window or configure explicit dedup_key extraction |
| Missing severity | Ensure severity field maps to recognized values: critical, high, medium, low, info |
| Rate limit exceeded | Increase rate limit in webhook settings or reduce alert volume at source |
| Payload too large | Keep payloads under 100KB; large fields are automatically truncated |
Best Practices
- Use HMAC authentication when available for stronger security
- Test with sample payloads before enabling in production
- Set appropriate severity thresholds for auto-RCA to reduce noise
- Enable correlation to reduce alert fatigue from cascading failures
- Monitor delivery logs to catch integration issues early
- Use explicit dedup keys when your platform provides stable alert identifiers