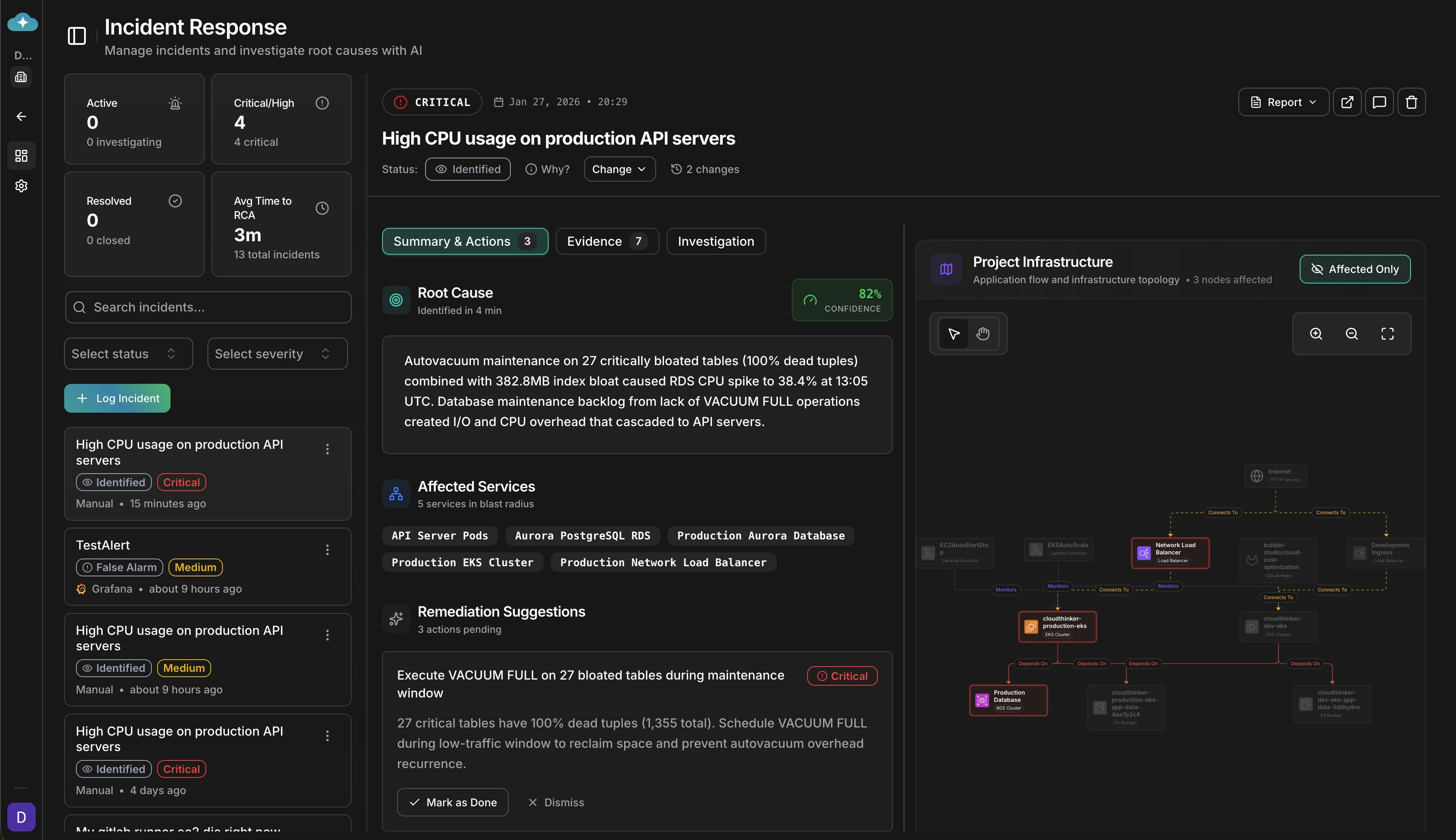
CloudThinker Incidents dashboard showing AI-powered root cause analysis in action
AI That Investigates
CloudThinker Incidents is AI-native. The AI isn’t a chatbot bolted onto an existing product—it’s the foundation of how incidents are analyzed and resolved.Hypothesis-Driven Investigation
The AI forms theories about what went wrong and systematically tests each one against your data, tracking which hypotheses are confirmed or ruled out.
Transparent Reasoning
Every step is visible in real-time. See what the AI checked, what it found, and the path it took to reach its conclusion. No black box.
Structured Evidence
Metrics with before/after comparisons, logs with timestamps, deployment changes with time-to-incident calculations—all organized into a coherent chain.
Confidence Scoring
Not every investigation reaches certainty. Confidence scores tell you whether you’re looking at a definitive answer or a hypothesis that needs verification.
How It Works
1
Incident Created
An incident is created manually, via API, or automatically when webhook alerts arrive from your monitoring tools.
2
Investigation Begins
An AI agent immediately starts investigating—no waiting, no manual trigger required.
3
Hypotheses Tested
The agent forms theories (“memory leak in auth service”, “recent deployment regression”, “exhausted connection pool”) and tests each one.
4
Evidence Gathered
Metrics, logs, traces, configurations, and deployments are collected and organized with timeline correlation.
5
Root Cause Identified
The AI identifies the root cause with confidence scoring and transparent reasoning you can verify.
6
Remediation Suggested
Prioritized action steps are generated—from critical fixes to improvements—ready for your team to execute.
Topology Awareness
Your services don’t exist in isolation. When your auth service fails, everything downstream fails too—checkout breaks, mobile apps throw errors, and support tickets spike across seemingly unrelated features. CloudThinker understands your infrastructure topology. When an incident occurs, the AI automatically:- Identifies affected services using your service dependency map
- Calculates blast radius showing what’s broken and what’s impacted
- Investigates with context knowing that payment depends on auth, which depends on Redis, which runs on a specific cluster
Connect Everything You Already Use
CloudThinker integrates with the monitoring tools your team already relies on. We support webhooks from 15+ platforms:| Platform | What’s Supported |
|---|---|
| PagerDuty | Native field mapping for alert details and priorities |
| Datadog | Metrics, alerts, and event correlation |
| Prometheus / Alertmanager | Kubernetes-native monitoring |
| AWS CloudWatch | Native support for AWS infrastructure alerts |
| Opsgenie | Priority and description extraction |
| New Relic, Grafana, Splunk, Dynatrace, Sentry | And more |
Continuous Learning
Every incident is an opportunity to get better. CloudThinker’s agent memory system captures investigation patterns so the AI improves over time. When the agent discovers that a particular metric query is useful for diagnosing memory issues, or that a specific log pattern indicates a connection pool problem, those techniques become part of its toolkit. Your team’s operational knowledge—the hard-won insights from years of debugging production systems—gets preserved and applied automatically.Next Steps
Ready to start investigating incidents? Set up incident ingestion from your monitoring tools:Webhook Integrations
Connect your monitoring platforms to auto-create incidents. Configure field mappings for PagerDuty, Datadog, Prometheus, CloudWatch, and 10+ more platforms.