The Cost of Manual Cloud Operations
Cloud operations teams spend countless hours on routine maintenance tasks: security audits, cost reviews, compliance checks, and resource cleanup. These tasks are critical but predictable—and they consume 40-60% of engineering capacity without delivering strategic value. Traditional approach challenges:- Repetitive manual work: Weekly security audits take 4-6 hours per account, scaling to 60+ hours for enterprises with 15+ accounts
- Inconsistency across environments: Different engineers interpret guidelines differently; compliance gaps appear when expertise concentrates in individuals
- Reactive firefighting: Issues surface during crisis moments (compliance audit, cost spike, security breach) rather than being caught proactively
- False positives everywhere: Manual scripts flag legitimate backup resources as orphaned, or miss context-aware risks entirely
What Are CloudKeepers?
CloudKeepers are autonomous pilots that enforce guardrails for cost, security, and operational health. They continuously scan your cloud infrastructure on a schedule you define, identify drift and misconfigurations, and surface intelligent recommendations with step-by-step remediation playbooks. Two specialized pilots:- CostOps: Identify unused resources, right-sizing opportunities, and cost anomalies with context-aware analysis
- SecurityOps: Detect IAM misconfigurations, exposed resources, encryption gaps, and compliance risks
The CloudKeepers Workflow
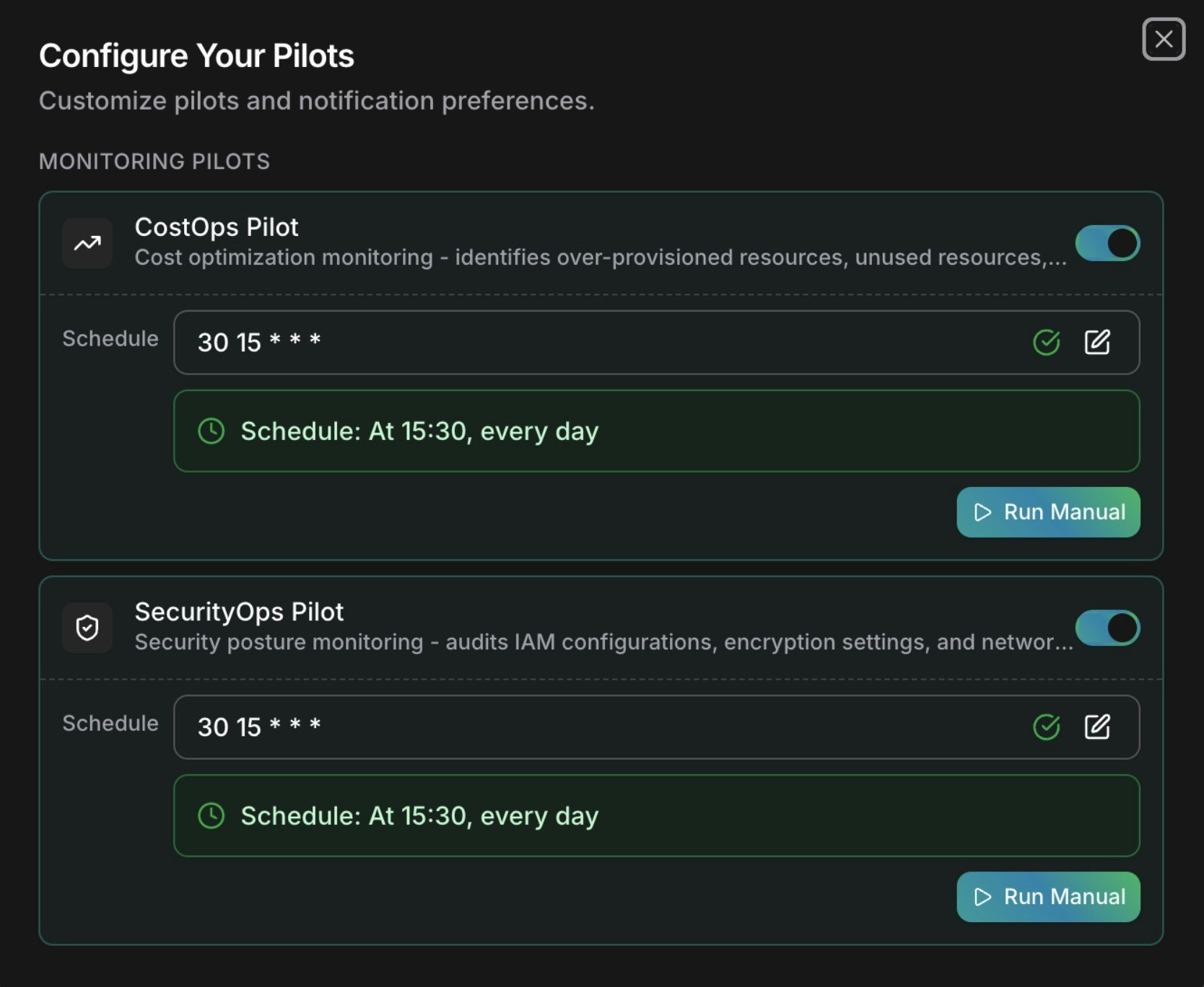
Configure CloudKeepers pilots
Open CloudKeepers and select Configure CloudKeepers. Enable the CostOps and SecurityOps pilots.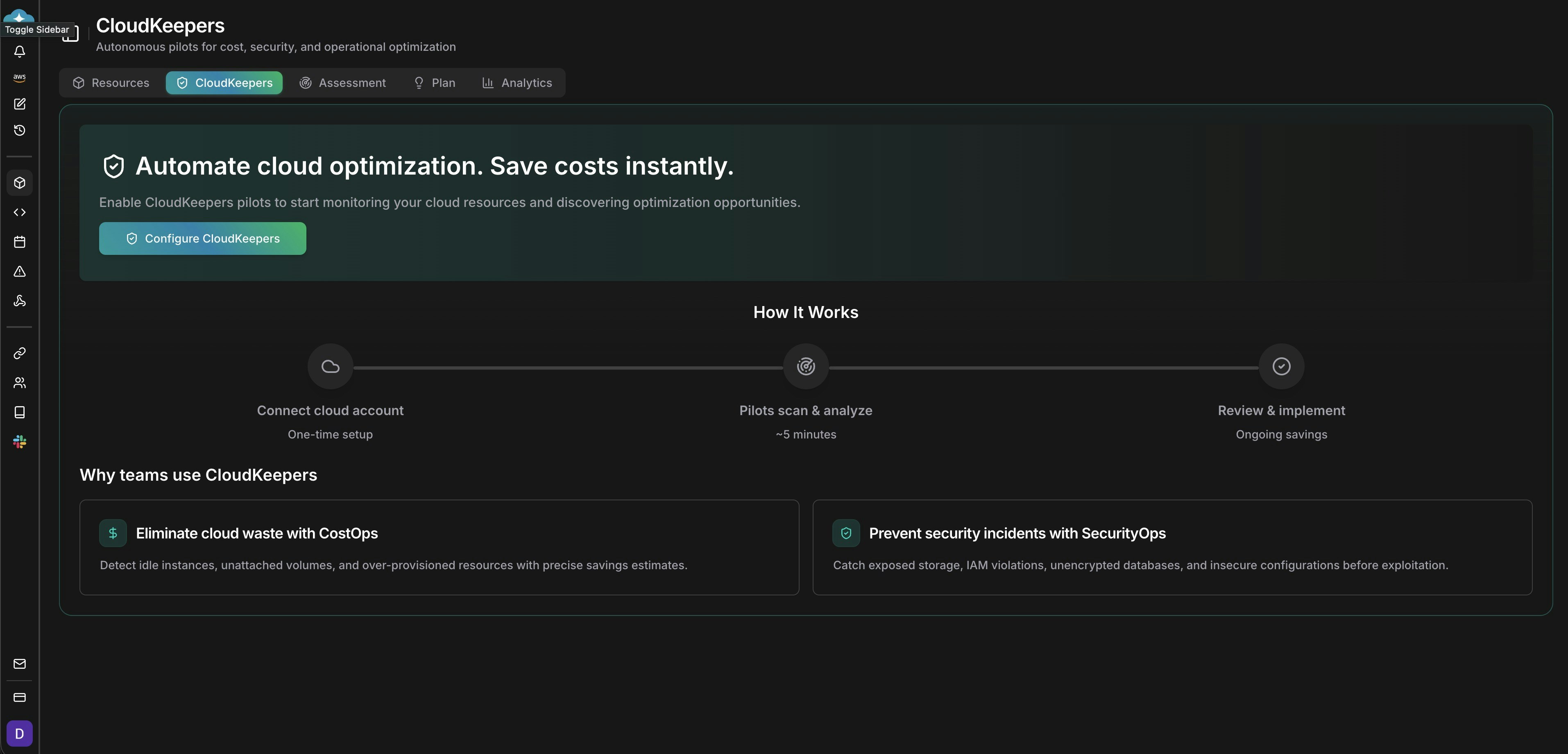

CloudKeepers landing page with pilot configuration
Set execution schedules
Define cron-style schedules for automated scans (e.g., daily at 15:30 UTC, weekly on Fridays at 08:00). You can also trigger manual scans on-demand.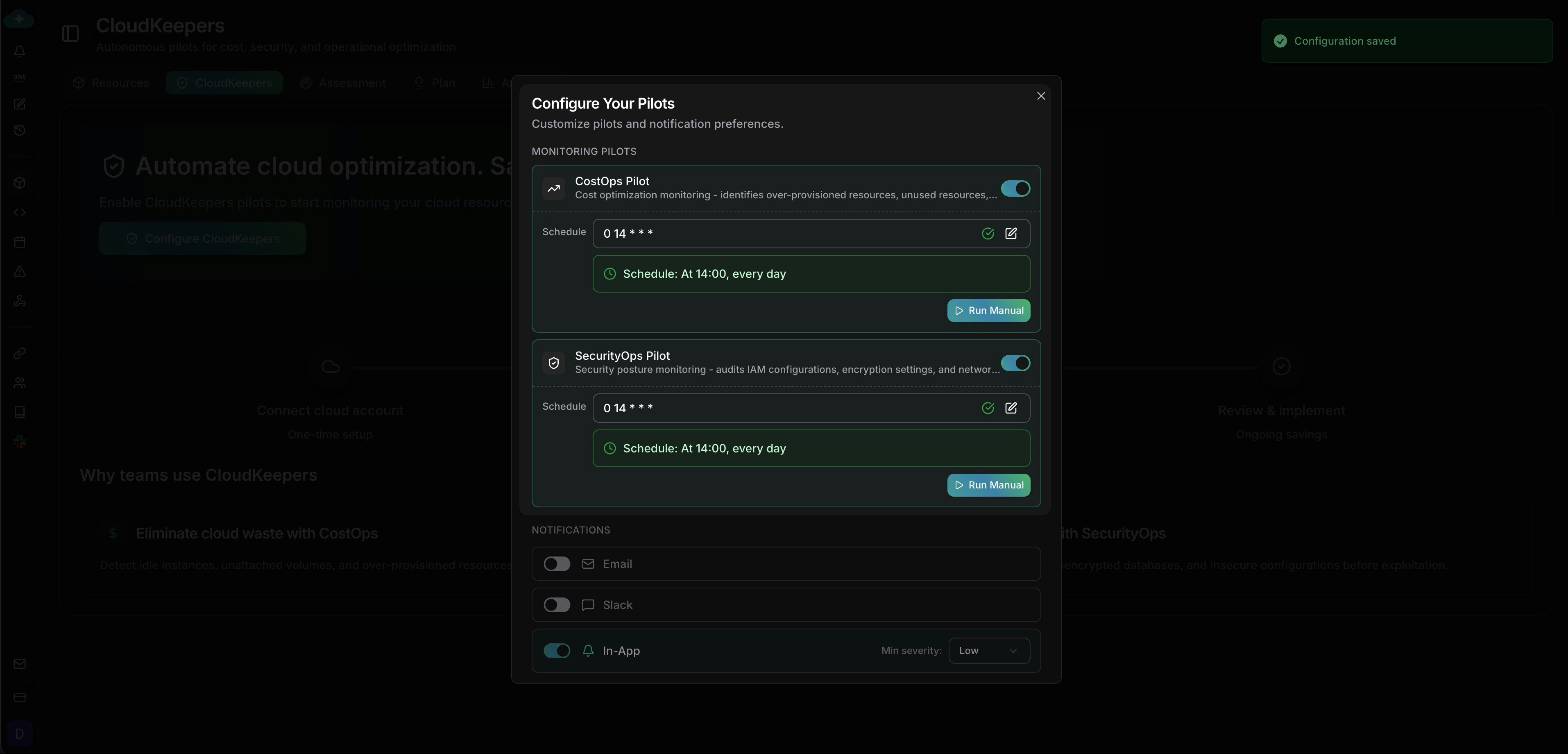

Set scan schedules for CostOps and SecurityOps pilots
Configure alerting thresholds
Choose notification channels (Email, Slack, In-App) and set minimum severity levels per channel to avoid alert fatigue.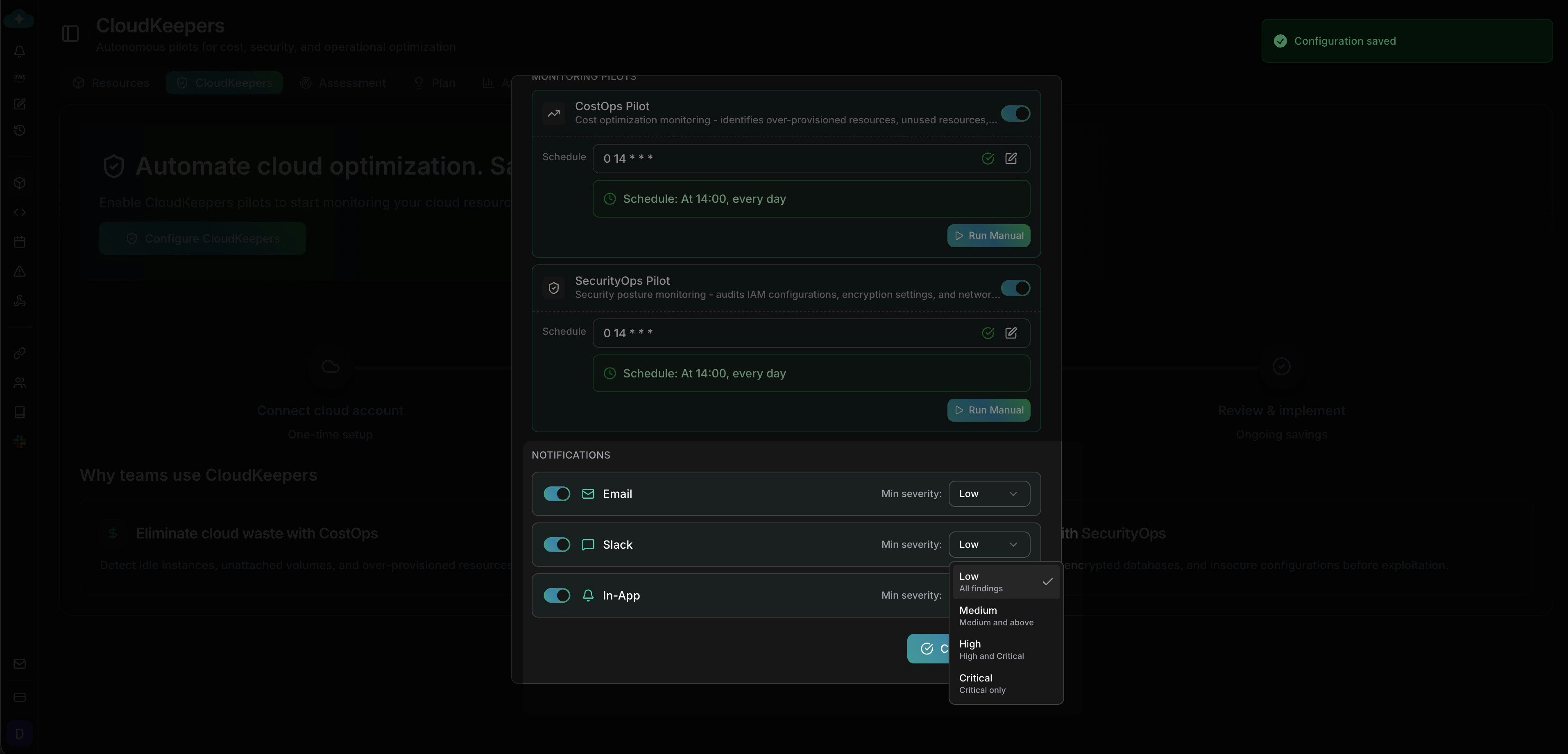

Configure notifications by channel and severity
Review findings
Monitor the Findings dashboard showing trend charts, total count, critical/high items, and potential savings. Review Recent Findings organized by pillar.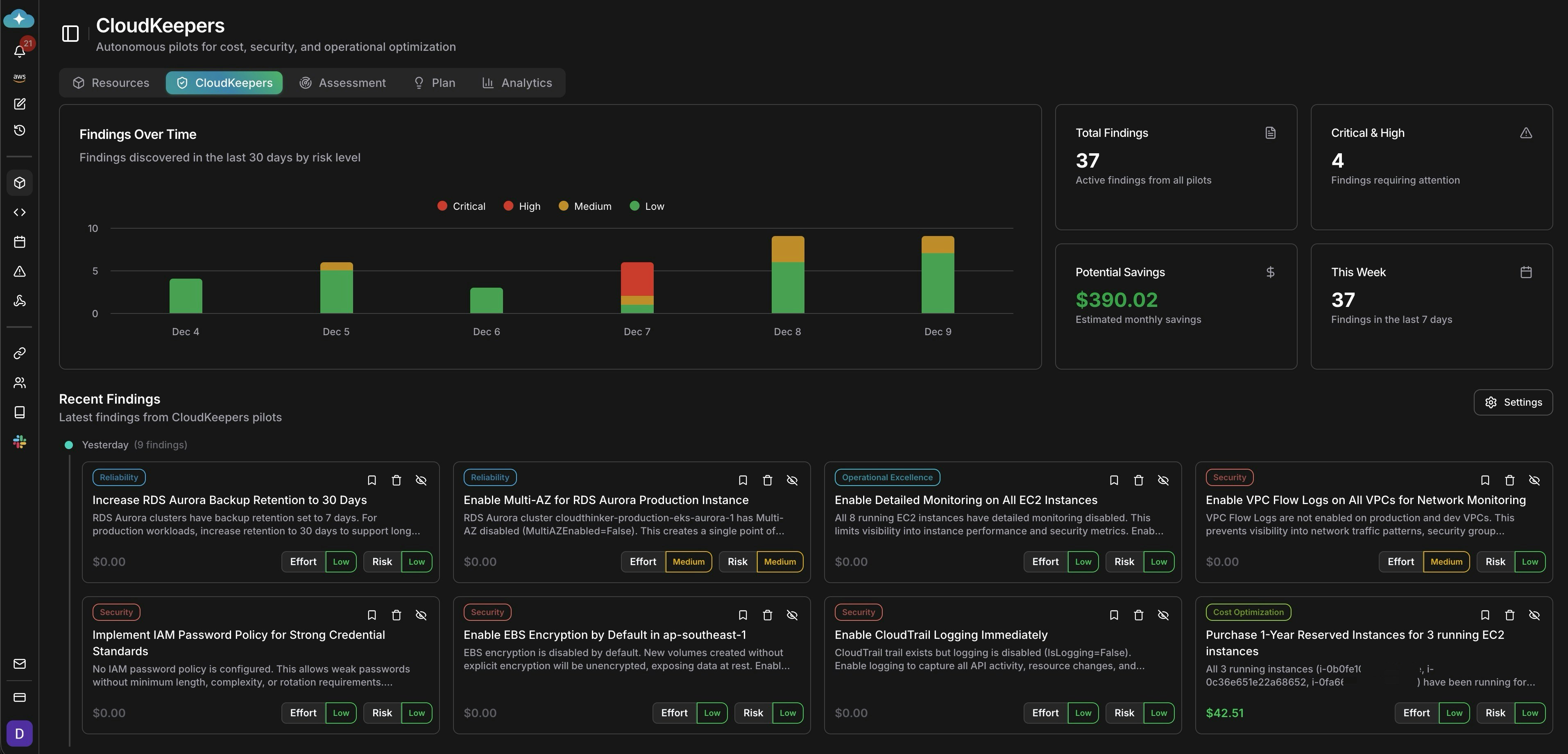

Findings dashboard with savings and severity breakdown
Drill into recommendations
Open any finding to see impact analysis, estimated cost/security impact, effort level, and step-by-step implementation guidelines.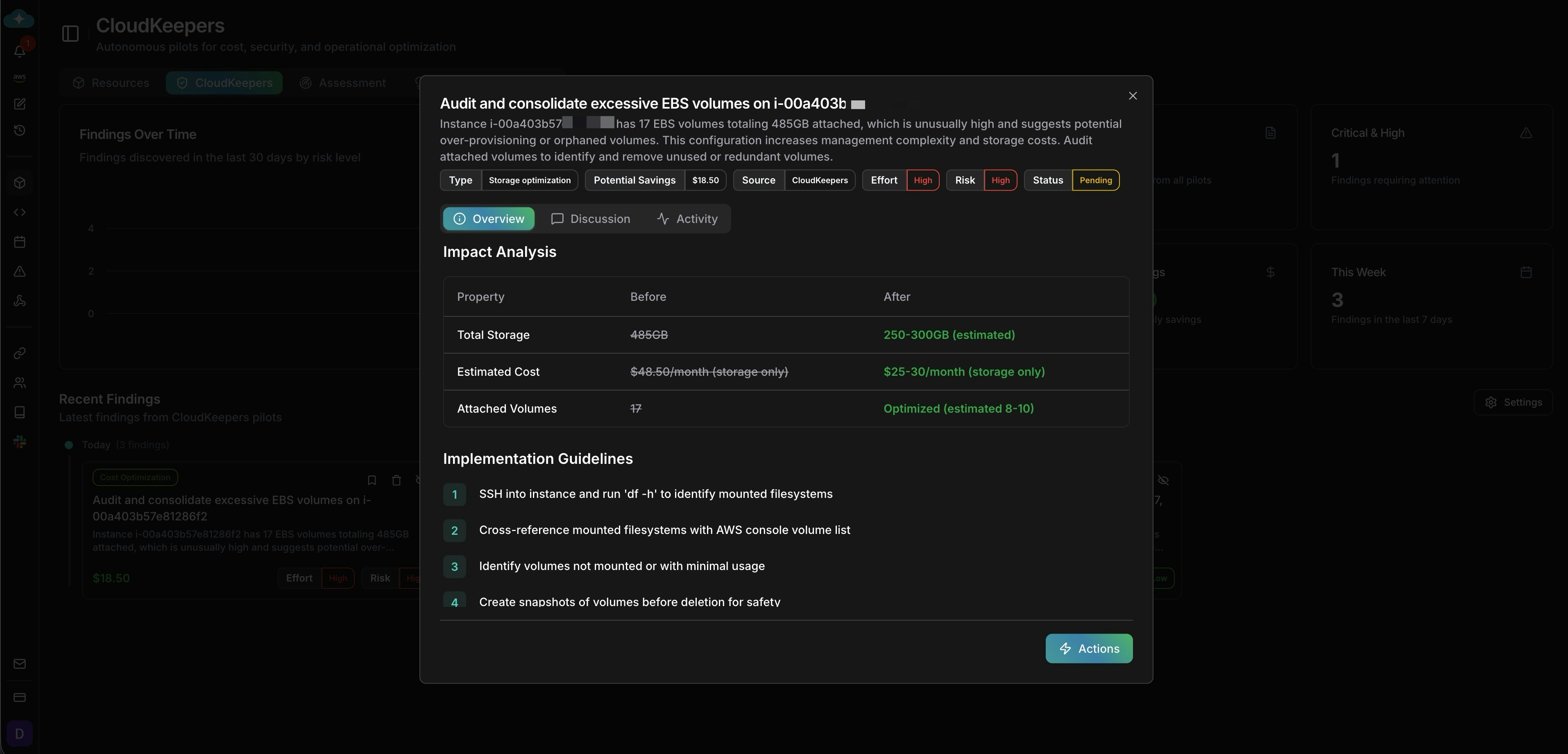

Detailed recommendation with impact analysis
Take action
From the Actions modal, choose how to proceed: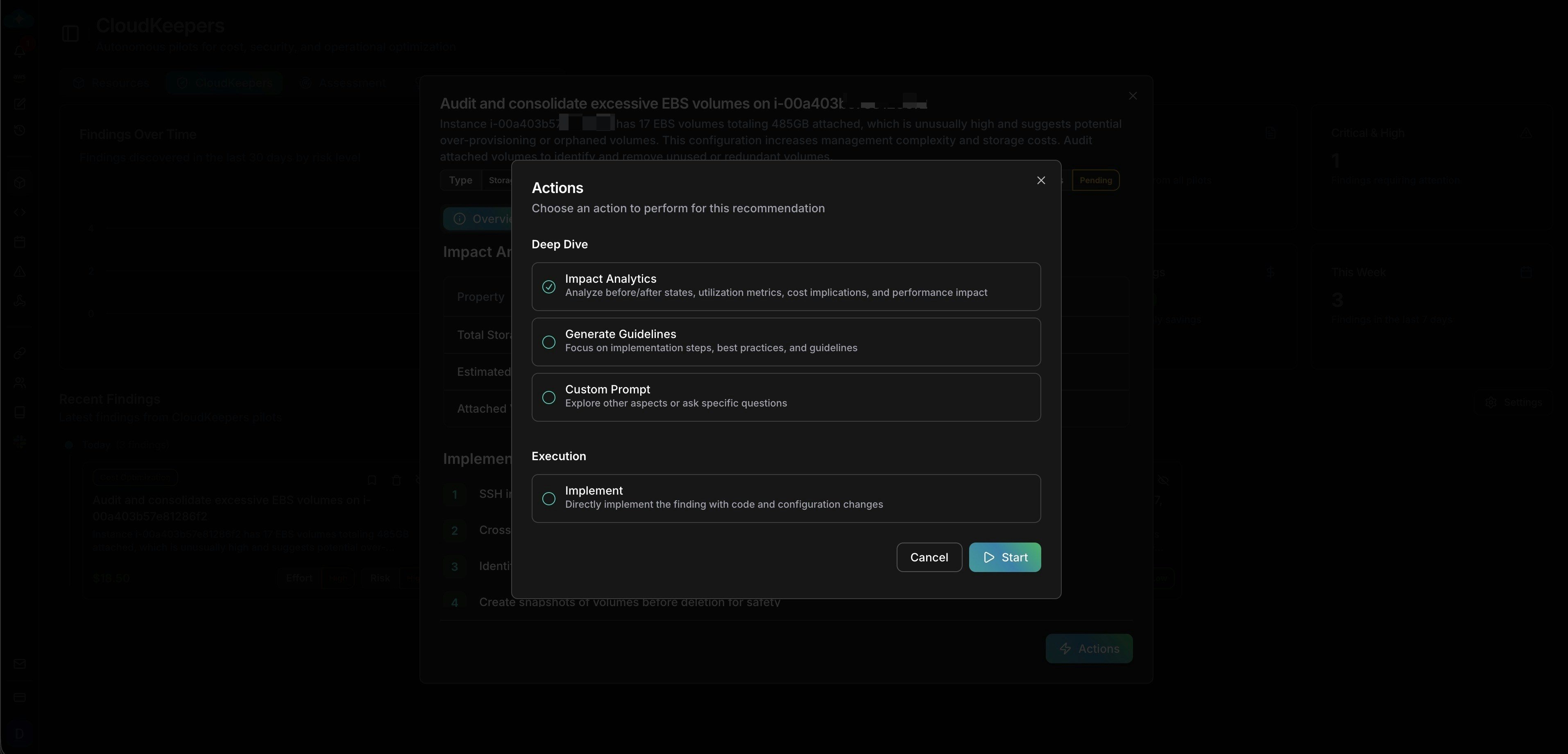
- Run Impact Analytics for deeper cost/risk analysis
- Generate Guidelines to create shareable runbooks for your team
- Ask Custom Question to explore edge cases with the AI agent
- Save to Plan to move findings into your governance workflow

Action options for each finding
Use Case 1: Proactive Cost Optimization with CostOps
Scenario: Your infrastructure has grown organically over 18 months. You’re aware costs are climbing, but pinpointing what’s actually unused (vs. reserved for disaster recovery or testing) requires deep investigation. Your CostOps team lacks the bandwidth to do monthly audits. CostOps pilot discovers:- Underutilized compute instances: 8 EC2 instances running at 5-15% average CPU (ideal candidates for right-sizing or shutdown)
- Orphaned storage: 12 unattached EBS volumes and snapshots accumulating $2,400/month
- Reserved capacity misalignment: Reserved instances for a deprecated service tier, losing $8,500/month in discounts
- NAT gateway inefficiency: Multi-AZ NAT setup processing minimal traffic, could consolidate to single gateway
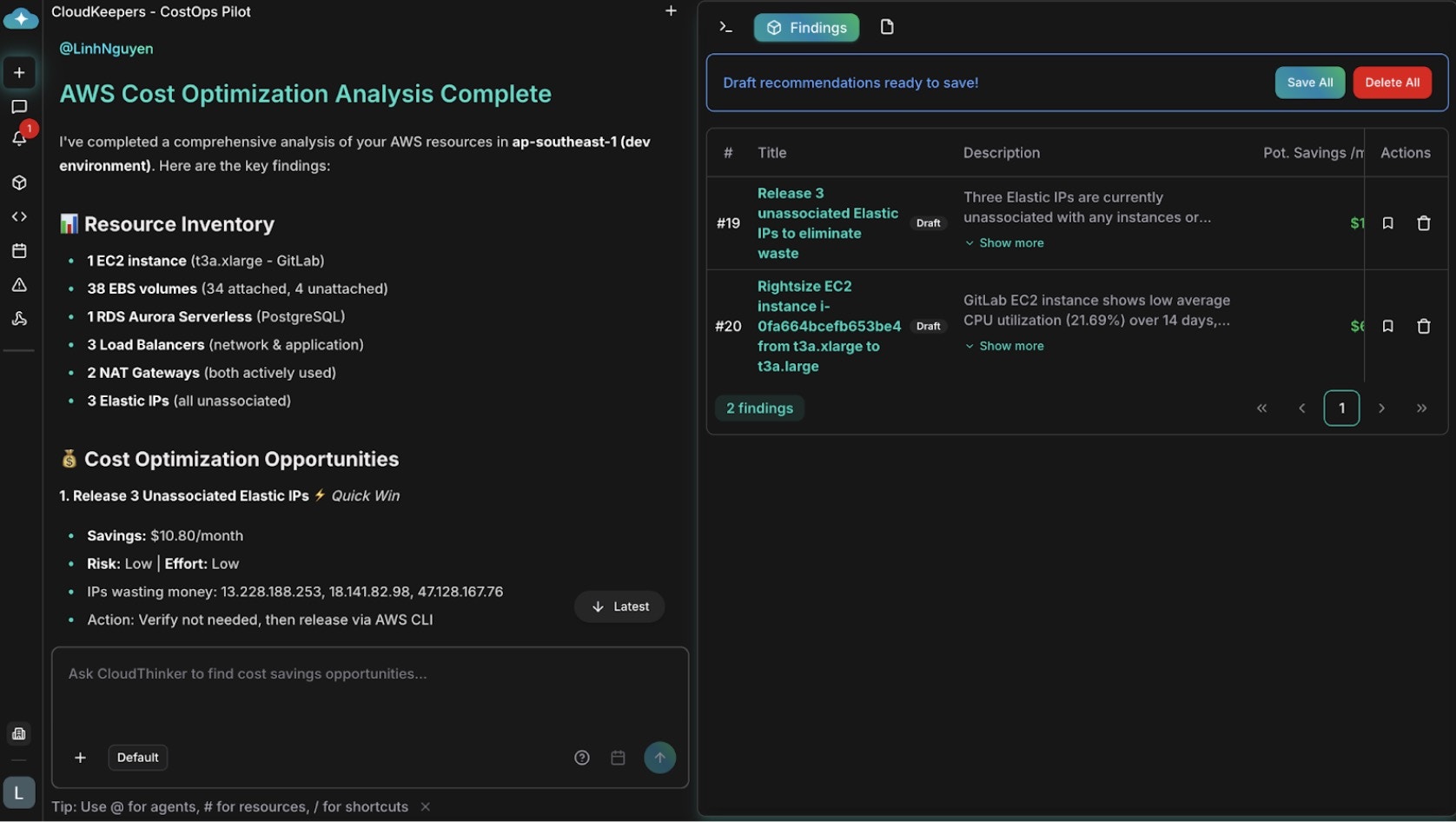
Cost optimization recommendations with savings analysis
Workflow:- Schedule runs: CostOps scan runs every Wednesday at 10:00 UTC
- Review findings: Your FinOps team reviews the dashboard each Thursday morning, seeing $14,200/month in identified savings
- Assess impact: For the EC2 right-sizing recommendation, generate impact guidelines and share with engineering to validate performance assumptions
- Save to Plan: Move high-confidence items (orphaned volumes, NAT consolidation) to Plan for approval and scheduling
- Execute and track: Plan workflows handle approvals, scheduling, and execution with full audit trails
Use Case 2: Continuous Security Posture Monitoring with SecurityOps
Scenario: Your organization maintains 12 AWS accounts across dev, staging, and production. Security compliance requires monthly audits, but inconsistent findings (different engineers miss different issues) and no standardized remediation creates gaps. A recent audit found IAM policies that hadn’t been reviewed in 8 months. SecurityOps pilot discovers:- IAM configuration drift: 23 IAM users/roles with overly-broad permissions (Developer policy attached when ReadOnlyAccess would suffice)
- Exposed resources: 2 S3 buckets with public read access (not intentional); 1 RDS database with public accessibility enabled
- Encryption gaps: 15 EBS volumes without encryption; 3 S3 buckets lacking default encryption
- Access anomalies: Root account used for day-to-day operations; detected unused service accounts not cleaned up
- Network exposure: 4 security groups allowing 0.0.0.0/0 SSH access (high-risk for compute; acceptable for ALBs)
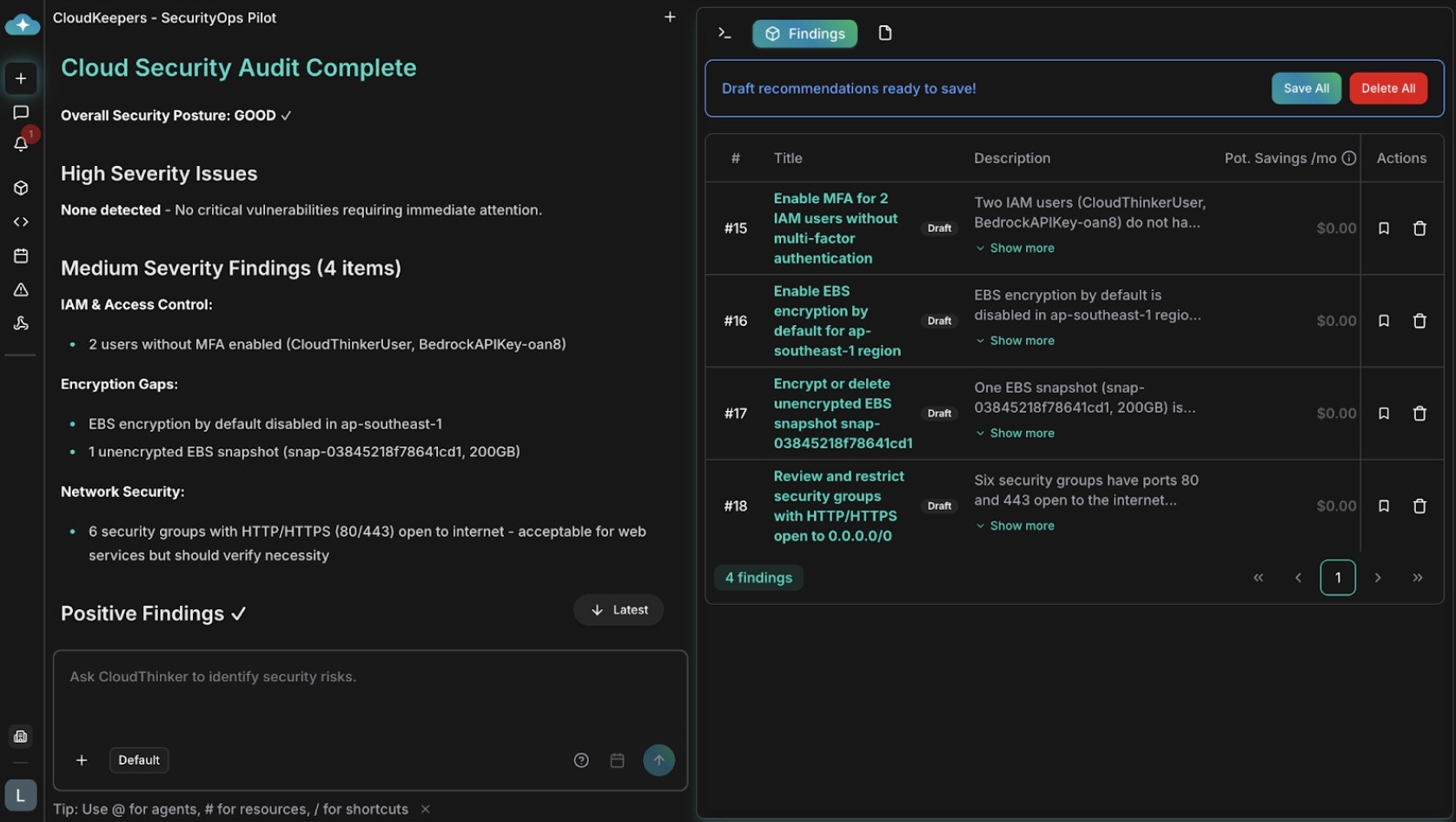
Security audit recommendations with remediation steps
Workflow:- Schedule runs: SecurityOps scan runs every Friday at 14:00 UTC (before your Monday compliance standup)
- Alert on critical findings: Your security team receives Slack notifications immediately for high-severity items (exposed database, root account in use)
- Review full report: Monday morning, your security team reviews the findings dashboard—23 medium-risk IAM findings, 2 critical exposure risks
- Generate playbooks: For the S3 bucket fix, generate implementation guidelines with AWS CLI commands; distribute to the owning team
- Save to Plan: Move findings requiring multi-team coordination (e.g., “remove root account access key”) to Plan for assignment, approval, and tracking
- Close findings: After remediation, mark findings as resolved or ignored to tune alert tuning
Integration with Plan for Governance
CloudKeepers findings begin as drafts in your infrastructure view. When you’re ready to act, you save them to Plan, where they become work items with:- Full audit trails: Every finding, its status, and remediation steps are documented automatically
- Approvals and assignment: Route findings to the right teams (security, FinOps, platform engineering) for review and sign-off
- Execution tracking: Plan tracks status (pending, approved, in progress, completed) with timestamps and ownership
- Compliance evidence: For audits, Plan provides timestamped records of when issues were identified and how they were resolved
Why CloudKeepers Beat Manual Processes
| Dimension | Manual Audits | CloudKeepers |
|---|---|---|
| Execution frequency | Monthly (if lucky) | Daily/weekly—continuous guardrails |
| Time investment | 4-8 hours per session | 2-5 min setup; 15-30 min weekly review |
| Consistency | Varies by engineer | Identical analysis every run |
| Context understanding | Relies on engineer judgment | Domain expertise baked into agents |
| Scaling with accounts | Linear growth (4-6 hrs per account) | Constant time regardless of scale |
| False positives | High (scripts miss context) | 95% reduction via intelligent filtering |
| Issue detection time | Weeks to discovery | Hours to detection |
| Knowledge transfer | Lost when experts leave | Persistent in agent behavior |
| Audit evidence | Manual documentation | Automatic comprehensive logs |
Getting Started
- Open CloudKeepers in your workspace
- Configure pilots: Enable CostOps and SecurityOps with your preferred schedules
- Set notifications: Choose channels and severity thresholds
- Run your first scan: Manually trigger a scan to see findings immediately
- Review and save: Save high-impact findings to Plan for team review and remediation tracking
CloudKeeper scheduler setup interface
Your cloud infrastructure can now maintain continuous guardrails autonomously, freeing your team to focus on strategic initiatives instead of operational toil. Learn more: CloudKeepers Documentation